International maritime transport covers over 80% of world trade and is the most efficient and cheapest method of transportation for most goods.
IMO (International Maritime Organization) the specialized agency of the United Nations in charge to promote maritime cooperation between member countries and to guarantee the safety of navigation and the protection of the marine environment) adopted in 2017 resolution MSC.428(98).
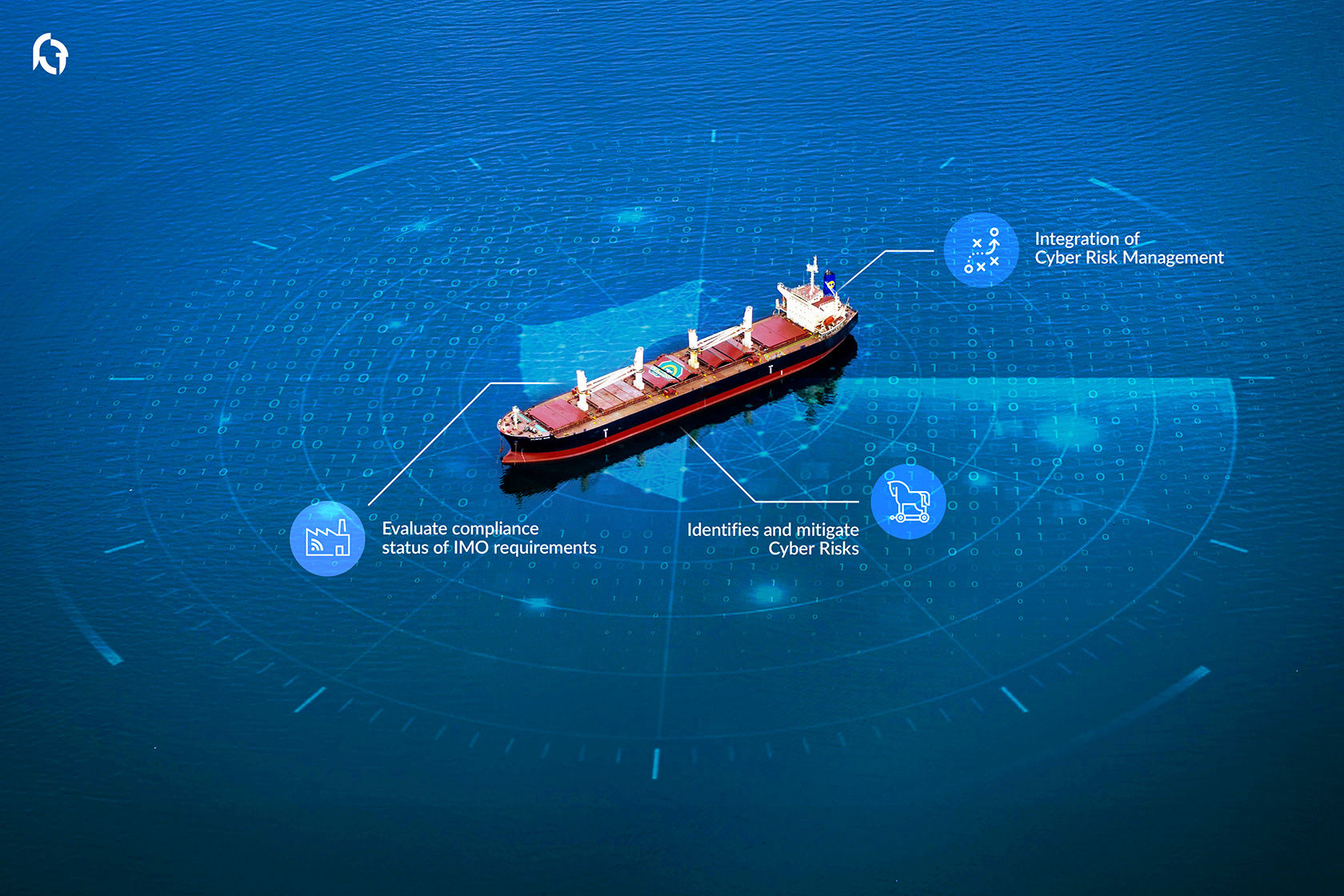
Resolution MSC.428(98) establishes that on-board Safety Management Systems must be integrated in order to take into account the aspects of cyber risk management related to on-board IT and OT system.
Cyber risk management should consider both cyber security and cyber safety because of their potential effect on personnel, the ship, environment, company and cargo.
Cyber security is concerned with the protection of IT, OT, information and data from unauthorised access, manipulation and disruption.
Cyber safety covers the risks from the loss of availability or integrity of safety critical data and OT.
Resolution MSC.428(98) establishes that on-board Safety Management Systems must be integrated in order to take into account the aspects of cyber risk management related to on-board IT and OT system.
Cyber risk management should consider both cyber security and cyber safety because of their potential effect on personnel, the ship, environment, company and cargo.
Cyber security is concerned with the protection of IT, OT, information and data from unauthorised access, manipulation and disruption.
Cyber safety covers the risks from the loss of availability or integrity of safety critical data and OT.